This particular virus affected me personally, as I have hosted several websites with IX Hosting for many years. Some lay blame with them even though other hosting servers have been hit as well, but
I cannot complain about their service. I've always been completely satisfied with their servers, support and pricing. The following is a description of what happened that I found posted on a
forum:
"It's a nasty hack. The code is injected into compromised sites (IXWebhosting has been hit bad by this, including all 24 of my domains. They have been rooted by another process). When you visit,
it's a javascript that loads an "eoj" malware (detected by Kaspersky as a rootkit, but it's not a true version of a rootkit).
To see if you've had the malware installed, go to your system32 folder and look for a file called sysaudio.sys. There is a real file by that name, but it's actually located in system32\drivers. If
you see the file in system32, you've been hacked. Delete the file, and look under the "HKLM\software\microsoft\windows nt\currentversion\drivers32" key, with value and valuedata containing
"aux"="sysaudio.sys" or "aux2"="sysaudio.sys". Export (for safety), then delete these entries. That should fix things.
Also, look closely at your websites; the injection attack is a nasty piece of work. Look for fake .htaccess files redirecting search engines to a Russian Mafia hosted malware factory. If you go
direct, everything is normal. If you surf from search engines like Yahoo or Google, you get redirected to the bad guys.
Currently the site I'm working on is hosted on IXwebhosting.com a US company whose help desk, etc are located in east europe. Since august this year (after the Georgia conflict) the site has been
subjected to several attacks. Basically the intruders add a snippet of JS code to HTML files and then add PHP code in all PHP files. Moreover all the files have ownership changed to HTTPD:HTTPD
(server is Linux). After the last complaint, I was told by the help desk that basically the problem lies in the version of the program - not true, as I have been attacked on both v 2.0.2 and 2.6+ -
and that httpd:httpd appears when the attack has been caused by a php script (sidenote: previous attacks had changed ownership to ROOT:ROOT). As far as the latter point is concerned, I had read
that this kind of ownership change is only possible if/when someone has superuser access to the whole machine."
This info helped me a great deal. I would have never found the fake audio driver on my own, and I suspected but wasn't sure about the added PHP codes. The added code in the html pages was obvious.
Luckily I caught this immediately and shut the site down. Hopefully no one was infected, although my machines were, and the infection manifested itself in a very subtle way. Rather than the blatant
redirection typical with most hijackers, this script kept everything in tact except the actual links to the websites pulled up on a search. This could very easily go unnoticed, leaving the user to
believe it's just the result of bad addresses, domains that have changed hands, or clever SEO by portal sites. The following screenshots however show that on a search for "Minor Notes", the index
page, or home page comes up first in Yahoo :
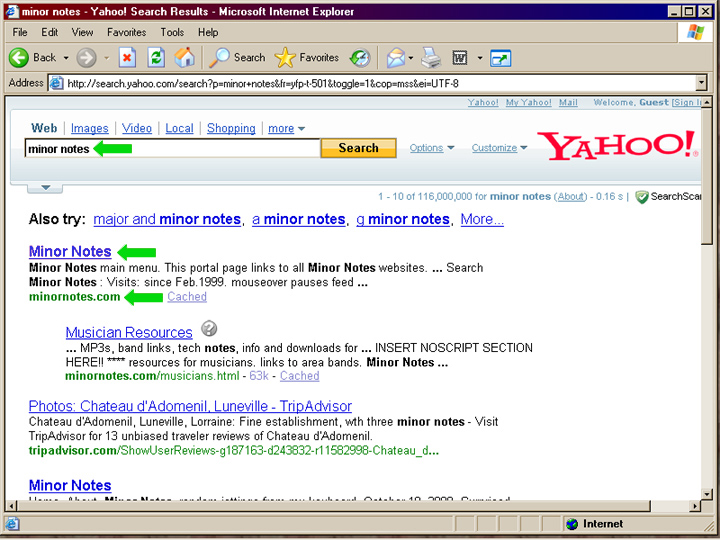
and this is on an infected machine:
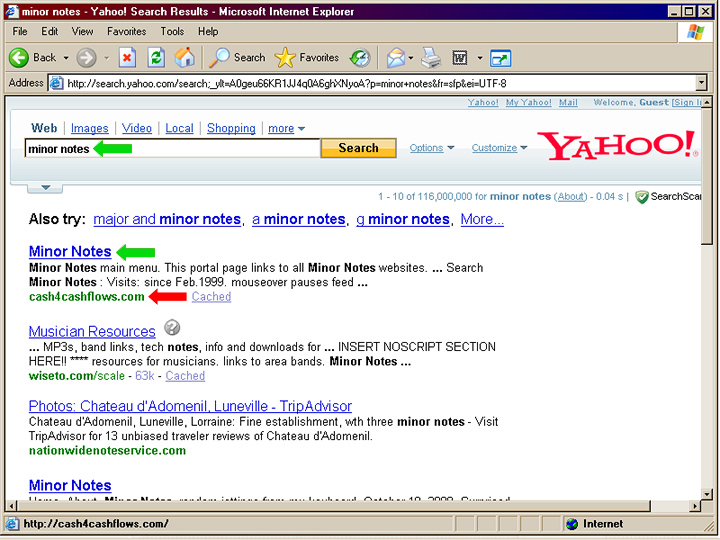
Everything looks normal in both searches, except that the second image shows the same search on the infected machine, and the actual link to Minor Notes has been replaced with "cash4cashflows.com"
(notice that the 2nd and 3rd results have also been altered). Some results further down were left alone as not to be TOO obvious. It did the same thing to Google and MSN, however DogPile was
unaffected. Subsequent identical searches showed that these addresses were different every time, on a rotation just like rotating banner ads to expand client base and revenues. Before fixing this
problem, I made a list of all participating websites in this marketing campaign. I sure I missed some, but these kept popping up over and over :
info.com
monstermarketplace.com
shopbrite.com
glimpse.com
everydayhealth.com
web-anitvirus.com
shopful.net
classified.livedeal.com
moxiesearch.com
findstuff.com
doubletakeart.com
summitracing.com
bestantispyware.com
surveyandgifts.com
revolutionhealth.com
cash4cashflows.com
eholidaycash.com
toseeka.org
insweb.com
bestwebchoices.com
wiseto.com
freefoodnow.org
couponmountain.com
hotjobs.com
lowpriceshopper.com
bizrate.com
Whether or not these companies are aware of what their marketing dollars are spent on every month, they all are guilty of negligence at the very least, and if I recognize their names in the future
I'll be certain to avoid their websites.
Anyway, on a user's machine this is pretty easy to remove by following the above instructions for finding and deleting the fake sysaudio file and its respective registry entries. For a server
infection, start first by removing the added code from ALL your html pages. It will look similar to this :
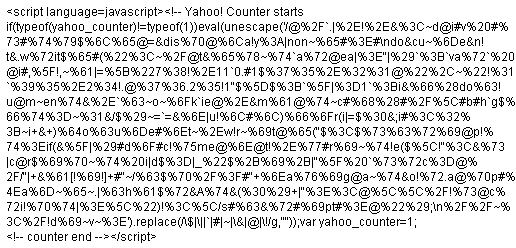
Then remove the code from ALL your PHP scripts that looks similar to this :

The PHP script will probably be one super-long line. It may also be necessary to change all your CHMOD settings and also your htaccess file.
USE YOUR BROWSER'S BACK BUTTON TO RETURN :



